Flask session demo, with kerberos and ldap auth
I have written a little demo application in python and flask. I might have use
of it in the future, particularly the group-based access to an endpoint. If
you need to write a small webapp that uses kerberos or ldap auth (from a form,
or basic auth), go clone my application from
gitlab!
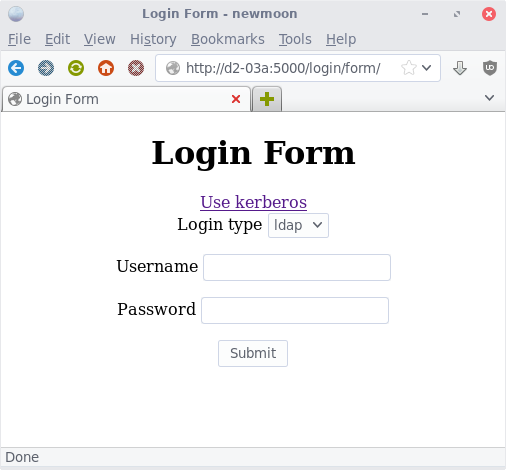
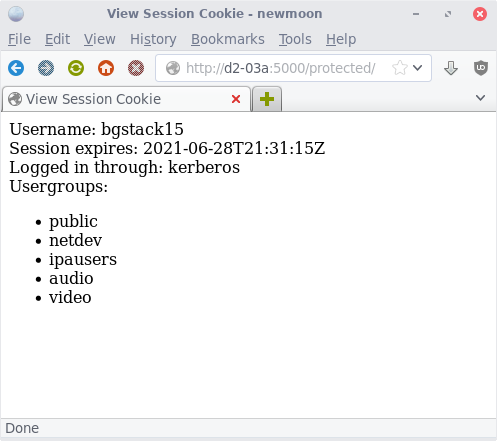
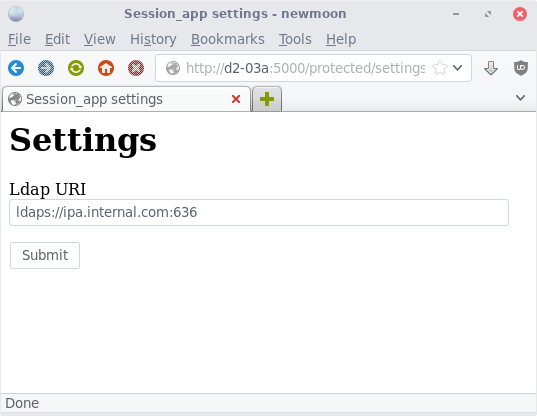 The way the application works is it accepts basic authentication at
/login/basic/, form authentication at /login/form/ (which defaults to
logintype=ldap) and kerberos www-negotiate at /login/kerberos. Any of these
methods, upon successful authentication, establish a session on the server
side and a cookie for the client to use. Use the cookie for each future
request. The admin can set how many minutes the session/cookie is valid for.
The full examples with curl are documented in
INTERACT.md.
The way the application works is it accepts basic authentication at
/login/basic/, form authentication at /login/form/ (which defaults to
logintype=ldap) and kerberos www-negotiate at /login/kerberos. Any of these
methods, upon successful authentication, establish a session on the server
side and a cookie for the client to use. Use the cookie for each future
request. The admin can set how many minutes the session/cookie is valid for.
The full examples with curl are documented in
INTERACT.md.
Start server in a separate shell session.
$ FLASK_APP=session_app.py FLASK_DEBUG=1 flask run --host 0.0.0.0
Reset any cookies and kerberos tickets.
$ kdestroy -A
$ rm ~/cookiejar.txt
Try visiting protected page without authorization.
$ curl -L http://d2-03a.ipa.example.com:5000/protected -b ~/cookiejar.txt -c ~/cookiejar.txt
requires session
Get kerberos ticket and then visit kerberos login url.
$ kinit ${USER}
$ klist
Ticket cache: FILE:/tmp/krb5cc_960600001_Hjgmv7lby2
Default principal: bgstack15@IPA.EXAMPLE.COM
Valid starting Expires Service principal
06/20/21 16:04:10 06/21/21 16:04:07 krbtgt/IPA.EXAMPLE.COM@IPA.EXAMPLE.COM
06/20/21 16:04:15 06/21/21 16:04:07 HTTP/d2-03a.ipa.example.com@IPA.EXAMPLE.COM
$ curl -L http://d2-03a.ipa.example.com:5000/login/kerberos --negotiate -u ':' -b ~/cookiejar.txt -c ~/cookiejar.txt
<meta http-equiv="Refresh" content="1; url=/protected/">success with kerberos
Visit protected page now that we have a session.
$ cat ~/cookiejar.txt
# Netscape HTTP Cookie File
# https://curl.se/docs/http-cookies.html
# This file was generated by libcurl! Edit at your own risk.
d2-03a.ipa.example.com FALSE / FALSE 0 user "bgstack15@IPA.EXAMPLE.COM"
d2-03a.ipa.example.com FALSE / FALSE 0 type kerberos
d2-03a.ipa.example.com FALSE / FALSE 0 timestamp 2021-06-20T20:06:15Z
#HttpOnly_d2-03a.ipa.example.com FALSE / FALSE 1624219691 session eyJfcGVybWFuZW50Ijp0cnVlLCJlbmRfdGltZSI6IjIwMjEtMDYtMjBUMjA6MDY6MTVaIiwidXNlciI6ImJnaXJ0b25ASVBBLlNNSVRIMTIyLkNPTSJ9.YM-fsw.ZeI4ec-d7D64IEJ9Ab4RfpXfLt4
$ curl -L http://d2-03a.ipa.example.com:5000/protected -b ~/cookiejar.txt -c ~/cookiejar.txt
<html>
<title>View Session Cookie</title>
Username: bgstack15@IPA.EXAMPLE.COM<br/>
Session expires: 2021-06-20T20:06:15Z<br/>
Logged in through: kerberos
</html>
For submitting to the form, pass in form data using fields `username`, `password`, and optionally `logintype` which can be defined within the application. An included option is `ldap`. Kerberos auth through the form is not supported.
curl -L -X POST http://d2-03a:5000/login/ --data 'username=bgstack15&password=qwerty' -b ~/cookiejar.txt -c ~/cookiejar.txt
Basic auth can be provided as a POST to /login/basic/.
$ curl -X POST -L http://d2-03a:5000/login/basic/ -b ~/cookiejar.txt -c ~/cookiejar.txt --user 'bgstack15'
Enter host password for user 'bgstack15':
<meta http-equiv="Refresh" content="1; url=/protected/">success with ldap
$ curl -X POST -L http://d2-03a:5000/login/basic/ -b ~/cookiejar.txt -c ~/cookiejar.txt --header "Authorization: Basic $( printf '%s' "${username}:${pw}" | base64 )"
<meta http-equiv="Refresh" content="1; url=/protected/">success with ldap
To set any settings that are currently supported by the /protected/settings/ page, you need to be a member of the ldap group "admins."
$ curl -L http://d2-03a:5000/protected/settings/ -b ~/cookiejar.txt -c ~/cookiejar.txt -X POST --data 'ldap_uri=ldaps://dns1.ipa.example.com'
Settings updated:<ul><li>LDAP_URI</li></ul><form action='/protected/settings/' method='get'><input type='submit' value='Return to settings'/></form>
Comments