View details of a certificate
Sometimes you need to inspect your certificate or certificate chain presented by a server. Here are several ways to do that.
Inspect certificate with web browser
If the certificate or cert chain in question is being used to present a web
site, you can visit the site in a browser, such as Firefox. Visit your site,
and select the padlock icon in the address bar beside the URL. 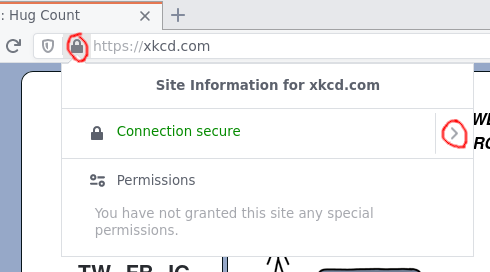 Select the arrow pointing to the right, and then select the "More information"
link.
Select the arrow pointing to the right, and then select the "More information"
link. 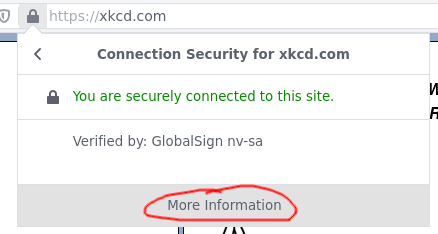 On the new modal window that appears, select the "View certificate" button.
On the new modal window that appears, select the "View certificate" button.
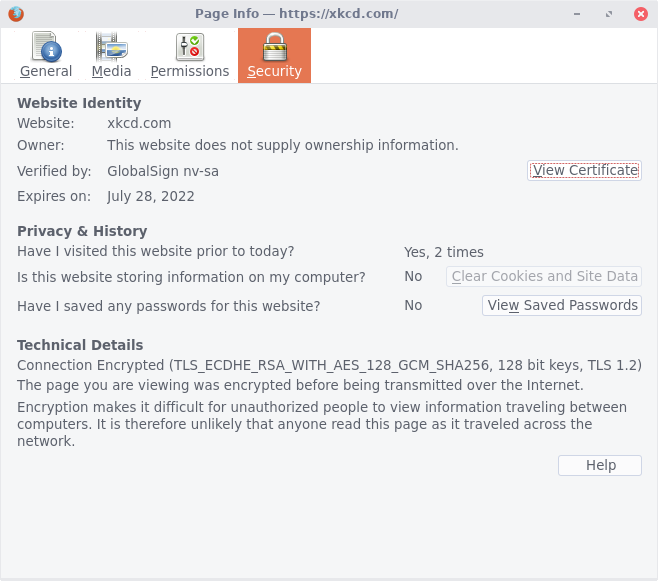 Firefox will show you the certificate and its chain (if Firefox knows about
it, or the web server presents the chain) for your inspection.
Firefox will show you the certificate and its chain (if Firefox knows about
it, or the web server presents the chain) for your inspection.
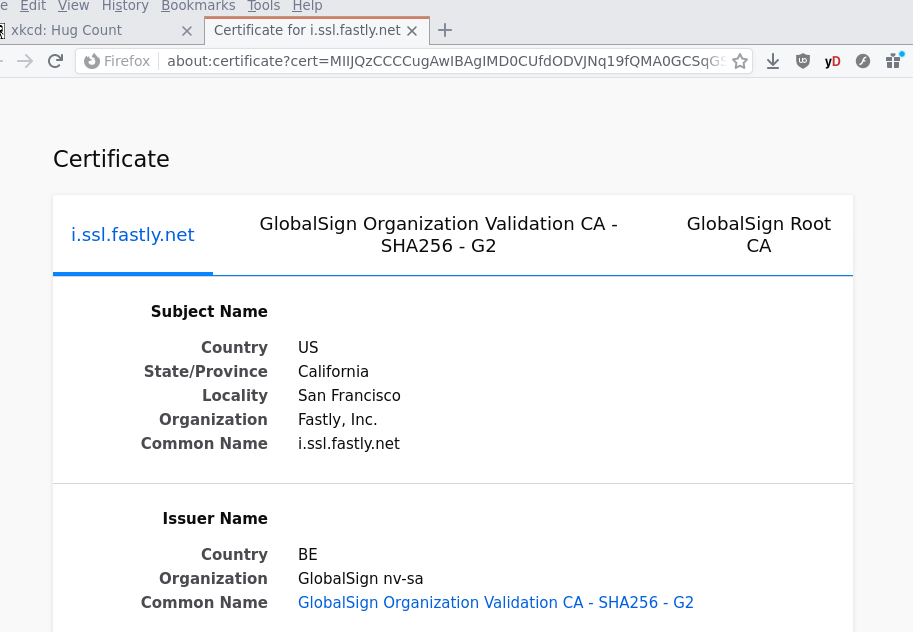
Inspect certificate chain with openssl command
The openssl reference implementation is available for both Windows and Linux through various means. Sufficiently high versions of openssl (>=1.0.1a) will be able to perform these tasks. Openssl can make network connections to https sites, and can also inspect files.
Inspect certificate chain presented by web server
The simplest way is to search for the descriptors provided by openssl natively with s_client. You can make sure the number and order of certificates is what you expect to make a complete intermediate-server cert chain.
$ echo "" | openssl s_client -connect xkcd.com:443 -showcerts 2>&1 | grep -iE '[si]:'
0 s:C = US, ST = California, L = San Francisco, O = "Fastly, Inc.", CN = i.ssl.fastly.net
i:C = BE, O = GlobalSign nv-sa, CN = GlobalSign Organization Validation CA - SHA256 - G2
1 s:C = BE, O = GlobalSign nv-sa, CN = GlobalSign Organization Validation CA - SHA256 - G2
i:C = BE, O = GlobalSign nv-sa, OU = Root CA, CN = GlobalSign Root CA
A well-behaved web server will present, at a minimum, the server certificate and all intermediate certificates. Serving the root certificate is optional, because well-behaved clients will already trust the root certificate. You can also dump the whole chain to a file, so you can split it up and read each certificate with the commands farther down on this page.
$ echo "" | openssl s_client -connect xkcd.com:443 -showcerts > certchain.pem
Inspect certificate in a file
Openssl will only read one certificate per file! If you have a certificate chain in a file, split it into multiple files before running these commands.
$ openssl x509 -in cert1.pem -noout -subject -issuer -dates -fingerprint -serial
subject=C = US, ST = California, L = San Francisco, O = "Fastly, Inc.", CN = i.ssl.fastly.net
issuer=C = BE, O = GlobalSign nv-sa, CN = GlobalSign Organization Validation CA - SHA256 - G2
notBefore=Jun 16 18:30:07 2020 GMT
notAfter=Jul 28 18:43:49 2022 GMT
SHA1 Fingerprint=7A:63:0B:5F:F6:72:E8:4D:70:B7:8B:45:1D:CF:27:94:AF:2C:F1:9A
serial=0F40947DD38354936AD7D7D0
Comments