Freeipa service account to join systems unattended
If you want to have systems join, or enroll in , FreeIPA, unattended, you need a few configurations. Run these on an ipa master. Establish a service account. I will use "domainjoin."
echo "thisisdapassword" | ipa user-add --first="domain" --last="join" --cn="domainjoin" --password --displayname="domainjoin" domainjoin
Remove the user from the default group of ipausers. We will add it to a new service accounts group.
ipa group-remove-member --users=domainjoin ipausers
ipa group-add service-accounts
ipa group-add-member --users=domainjoin service-accounts
I ensured this user existed by sshing in to a dev box, and it prompted me to
change its password. So it is worth doing that at least once before the next
steps. Or maybe a kinit would work and ask for a new password. I had to modify
my hbac rule "allow_all" by changing it to work against only certain groups
("public" and "admins") in the web interface. I didn't quite figure out how
the command line syntax worked for that. But I had to do that to lock out the
service account from being able to access services on hosts, i.e., log in.
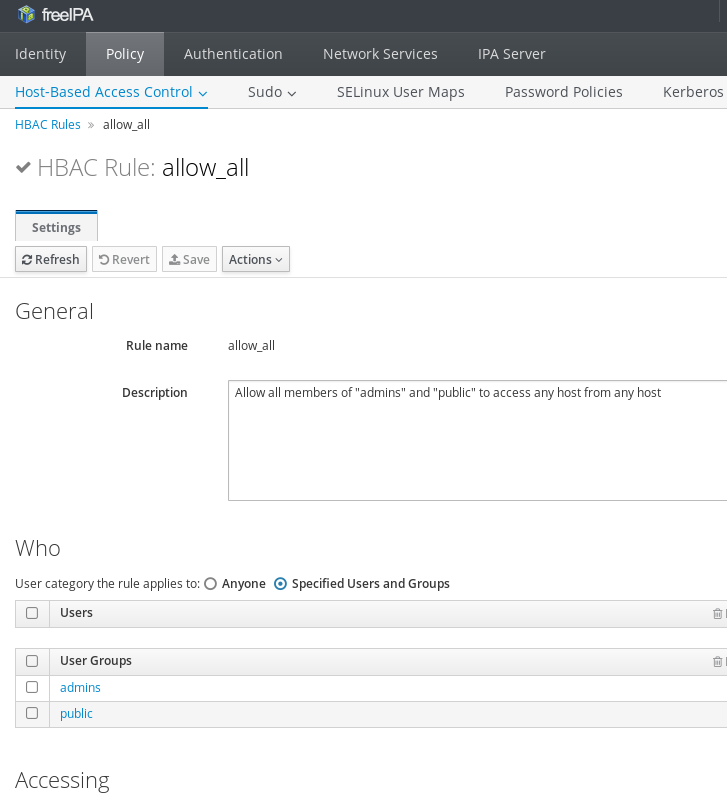 It might be as easy as adding specific users and groups to the hbac
rule, but I don't know for sure. In the web interface, I first had to change
the radio button for "Applies to specified users and groups," hit the save
button, and then I could add the specific groups. So it's probably a boolean I
didn't discover in the ipa help hbac pages. So with the service account
now locked out of systems, we need to give it the permissions it needs to join
hosts. Thankfully, the ipa guys have already built some relevant rbac entities
for us! Add the user to the role "Enrollment administrator."
It might be as easy as adding specific users and groups to the hbac
rule, but I don't know for sure. In the web interface, I first had to change
the radio button for "Applies to specified users and groups," hit the save
button, and then I could add the specific groups. So it's probably a boolean I
didn't discover in the ipa help hbac pages. So with the service account
now locked out of systems, we need to give it the permissions it needs to join
hosts. Thankfully, the ipa guys have already built some relevant rbac entities
for us! Add the user to the role "Enrollment administrator."
ipa role-add-member "Enrollment Administrator" --users=domainjoin
Just for your information, this role is mapped to a particular privilege, which is mapped to a set of permissions.
[root@dns1|/root]# ipa role-show "Enrollment Administrator"
Role name: Enrollment Administrator
Description: Enrollment Administrator responsible for client(host) enrollment
Member users: domainjoin
Privileges: Host Enrollment
[root@dns1|/root]# ipa privilege-show "Host Enrollment"
Privilege name: Host Enrollment
Description: Host Enrollment
Permissions: System: Add krbPrincipalName to a Host, System: Enroll a Host, System: Manage Host
Certificates, System: Manage Host Enrollment Password, System: Manage Host Keytab, System: Manage Host
Principals
Granting privilege to roles: Enrollment Administrator
For the service account to create new hosts, which is important when enrolling the host to the domain, it needs a specific permission that is excluded by default, according to reference 1.
ipa privilege-add-permission "Host Enrollment" --permissions="System: Add Hosts"
And now, you should be ready to run this on any client machine to join!
sudo ipa-client-install --hostname="$( hostname --fqdn )" --mkhomedir --configure-firefox --principal=domainjoin --password=thisisdapassword -U
Reference
Ok, this is enough do do an enrollment (HostEnrol is not a default role). What it lacks is the ability to add a new host entry. You can add this ability by adding the 'Add Hosts' privilege to the 'Host Enrollment' privilege. On the command line like this:
$ ipa privilege-add-permission 'Host Enrollment' --permissions='AddHosts'
Note that this is expected. We delegate as few permissions by default as possible. The expectation is that a higher-level administrator pre-creates the hosts that should be allowed to be enrolled and this delegated role can enroll them. rob
Auxiliary notes
So I didn't actually use anything from this, but it seemed interesting and I'm saving it for myself for later. FreeIPA — Linux Guide and Hints
Comments